Rancher & Keycloak authentication backend setup

Rancher v2.X KeyCloak Authentication Backend Configuration
Ranchers official documentation about how to configure the Rancher & KeyCloak setup is fine but definitely not sufficient to successfully configure it. That's why every single required step is documented down here.
KeyCloak Configuration
Steps are based on master realm for the Rancher client. Nevertheless, it would sometimes absolutely make sense to use a custom KeyCloak realm.
-
Login as
adminon KEYCLOAK Important: It's crucial that in KeyCloak the same username exists as you use as admin user on Rancher. Since I just use theadminaccount in this guide, this prerequisite is already achieved. -
Create a new client under KEYCLOAK
Client ID:https://rancher.example.com/v1-saml/keycloak/saml/metadataClient Protocol:samlRoot URL: Leave empty
-
Configure some more properties (every other property is set to its default value):
Name:rancherEnabled: ONLogin Theme:keycloakSign Documents: ONSign Assertions: ONName ID Format:usernameValid Redirect URLs:https://rancher.example.com/v1-saml/keycloak/saml/acsIDP Initiated SSO URL Name:IdPSSONameEvery other setting should be OFF
-
Next, continue with the client mappers. Add/update the following two additional ones:
- Username:
Name:x509 usernameMapper Type:User PropertyProperty:usernameFriendly Name: Leave emptySAML Attribute Name:uidSAML Attribute NameFormat:Basic
- Groups:
Name:groupsMapper Type:Group listGroup attribute name:memberOfFriendly Name: Leave emptySAML Attribute Name:BasicSingle Group Attribute: ONFull group path: OFF- Group attribute name can also be set as
member. If you have existing users from ldap fedration etc, better to usememberOfit works with both.
-
Enable Builtin Mappers
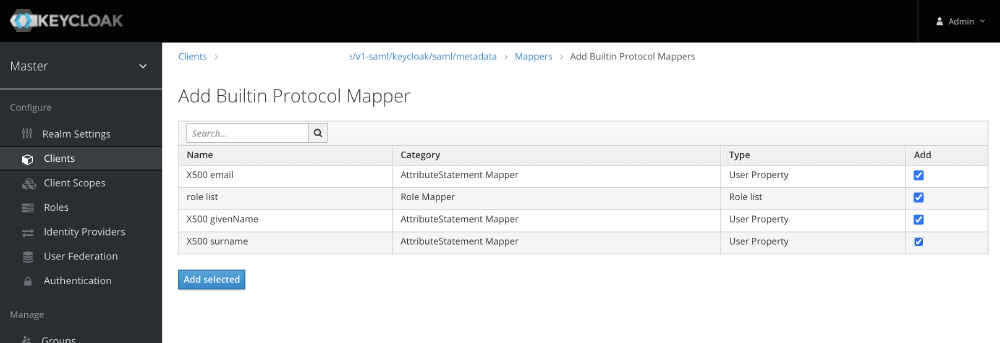
-
Since Rancher needs a private key and public certificate to sign the messages, you need to create one for this purpose or use any existing.
- To create new use the below command.
1 openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:2048 -keyout rancher-client.key -out rancher-client.cert -
Last but not least, you need to get the SAML Descriptior XML file.
- Access
https://KEYCLOAK/auth/realms/master/protocol/saml/descriptorand save this XML content to a file calledmetadata.xml.
OR
1 curl -k https://KEYCLOAK/auth/realms/master/protocol/saml/descriptor >metadata.xml- Since Rancher do not understand the
EntitiesDescriptortags Rancher Docs , copy all attributes from the<EntitiesDescriptor ...>tag and paste them in the<EntityDescriptor ...>tag one line below. Then remove theEntitiesDescriptortags on the first and last line. Example:- From this:
1<EntitiesDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:dsig="http://www.w3.org/2000/09/xmldsig#" Name="urn:keycloak"> 2 <EntityDescriptor entityID="https://KEYCLOAK/auth/realms/master"> 3 <IDPSSODescriptor ...... 4 ..... 5 </IDPSSODescriptor> 6 </EntityDescriptor> 7</EntitiesDescriptor>- To this:
1<EntityDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:dsig="http://www.w3.org/2000/09/xmldsig#" Name="urn:keycloak" entityID="https://KEYCLOAK/auth/realms/master"> 2 <IDPSSODescriptor ...... 3 ..... 4 </IDPSSODescriptor> 5</EntityDescriptor> - Save and close the
metadata.xmlfile.
- Access
-
Now it's time to create groups inside KeyCloak, which you afterwards would like to permit on Rancher. In our example:
- In case of using fedrated ldap server following must be configured in order to map groups from ldap to roles in keycloak.
- User Federation > Ldap >LDAP Mappers > Create New
Name:ldap-group-nameMapper Type:group-ldap-mapper
- User Federation > Ldap >LDAP Mappers > Create New
- Furter configure the following
LDAP Groups DN:cn=groups,cn=accounts,dc=ldap,dc=example,dc=comLDAP Filter:(cn=ldap_group_name)
- In case of using fedrated ldap server following must be configured in order to map groups from ldap to roles in keycloak.
-
Assign the group memberships for your KeyCloak user, which is named the same as your current Rancher admin account (in our case
admin). Add this user to the group by clickingEditon the related user ->Groups-> Select both just created groups (one by one) and clickJoin.
Important: This user needs to have all group memberships for groups, which you would like to permit on Rancher later on. That's because Rancher is not able to search for groups via SAML, it just knows the one from your user. 10. That's all for the KeyCloak configuration part - simple, right ;-)?... Now continue with the Rancher configuration.
Rancher KeyCloak Authentication Configuration
-
Access the Rancher GUI and navigate to
Security->Authentication. -
Select
KeyCloak(SAML) and set the properties according to the values down here:Display Name Field:givenNameUser Name Field:uid(this field must match theSAML Attribute Namevalue from the KeyCloak Rancher clientx509 usernamemapping!)UID Field:uid(this field must match theSAML Attribute Namevalue from the KeyCloak Rancher clientx509 usernamemapping!)Groups Field:memberOf(this field must match theGroup attribute namevalue from the KeyCloak Rancher clientgroupsmapping!)Rancher API Host:rancher.example.com
-
Next, upload the before created files:
Private Key:rancher-client.keyCA Certificate:rancher-client.crtMetadata XML:metadata.xml
-
Click on
Saveand a small window will open which redirects you to the KeyCloak Login mask. (Allow popup in your browser)
Enter the KeyCloak credentials and if everything was configured properly, the small window will close back again and you will be redirected and directly logged into Rancher. -
Now configure which groups can access Rancher by default without being specially granted on cluster/project basis.
ChoseAllow members of Clusters, Projects, plus Authorized Users and Organizationsand in the textfield/dropdown on the right, click the dropdown button and select which group will be able to access Rancher (e.g.rancher-admins). Do not enter the group name in the textfield and hit enter (or click on the suggested value in the dropdown) since then it's then added as user and not as group! Ensure that right under the group name there isGroupwritten in a light gray font and notUser. -
Finally click save and you will be good to go.
Test the KeyCloak login in a incognito browser window by accessing Rancher endpoint and clicking on Log In with KeyCloak (you will then be redirected to the KeyCloak authentication site.